
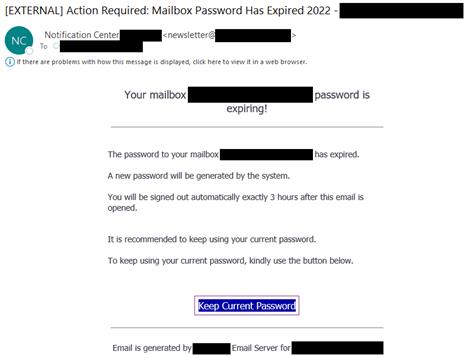
June 23, 2022 - The NJCCIC warns of a phishing campaign that has targeted New Jersey State employees with the intent to steal Microsoft 365 credentials. If successful, this ploy will allow cyber thieves to gain remote access, exfiltrate data, and deploy ransomware. At first glance, the email appears legitimate, as the sender’s display name is “Notification Center” and includes the target’s domain name. However, the sender’s actual email address includes the word “Newsletter”. If viewing this email on a mobile device, the actual email address is hidden, allowing only the sender’s spoofed display name to be shown, causing potential victims to be more inclined to act. In addition, the subject line indicates a false sense of urgency by using phrases such as “Action Required” and “Important Notification”, also going as far as including the target’s email address. Various red flags include, “mailbox password has expired” message displayed throughout the email, except for one instance of the “mailbox password is expiring.” The phishing email advises the target that their mailbox password has expired and directs them to click on the “Keep Current Password” link, which is linked to a phishing webpage with the New Jersey State branding. The target is prompted to entire their login credentials, at which point the threat actors steal the login credentials to commit further cyber-attacks. Although the phishing website has been removed, threat actors continue to register new domain names and impersonate legitimate and official websites, with intention to victimize targets.
If you have questions on cyber security training for employees, or taking the complexity out of managing passwords, call us at 609-642-9300, or email HelpMeNow@DiamondBC.net.
The NJCCIC recommends that users refrain from clicking links or opening attachments delivered in suspicious or unexpected emails, even those from known senders, and only submit account credentials on official websites. Any user whose account has been compromised, or may have potentially been compromised, is advised to change their password immediately for all accounts which share the same password. Users are also urged to consider a more secure method of multi-factor authentication (MFA) , such as an authentication app, biometric, or hardware token. Additionally, remove any unauthorized auto-forward, auto-delete, or reply-to rules created for compromised accounts. Organizations that identify compromised accounts on their networks are encouraged to lock the users’ accounts, identify any malicious emails sent during the time of compromise, and notify recipients. If mailbox auditing is enabled, review the logs to identify which mailboxes were accessed or had access attempts made without authorization. Email account compromises are often a precursor to ransomware infections. Efforts made to recover these accounts should also include analysis of any suspicious activity, such as attempts to elevate privileges, create new rules or users, move laterally, etc., as that could indicate wider network compromise.
Is your network secure? There could be vulnerabilities that you’re unaware of. Download our free e-book for tips on How to Protect Your Network.



